Regardless of how much we’d like to pretend otherwise, the Internet continues to be a place with an increasing number of privacy threats, and a false sense of hope is not going to keep you safe. Instead, you should have a clear plan on how to browse the Web and use all its services safely.
It becomes even more critical if you use the web for your professional or business needs. You need a multi-layer security system if you handle multiple accounts for your business. IP bans and additional costs are the last things you want to experience.
But how do you set up the safest way to browse the web? What technologies should you use? Do not worry; below we will explain everything you should know. Keep reading this article to help yourself stay extra safe on the Internet.
The Multi-Layer Security System for a Safer Web Browsing Experience
You would be wrong if you think using a VPN alone will keep you safe on the web. While VPNs offer a primary level of protection against security threats, you may face issues while handling multiple accounts. As you probably already know, IP bans and additional expenses are everyday struggles while using VPNs. Similarly, proxies alone are not going to help.
Considering this, we recommend a combination of the following methods to create the safest way to browse the web:
- A Virtual Private Network (VPN);
- High-quality Proxy Servers;
- A Multi-Accounting Antidetect Browser
Before we tell you how to set up these three technologies in conjunction, let’s have a quick look at how they work, their pros, and their cons.
VPNs – A Quick Introduction
Virtual Private Networks, better known as VPNs, are widely used to protect one’s identity while browsing the web. Instead of sending the request directly to a website/service, your Internet traffic would be tunneled through a Virtual Private Network. Similarly, the response from a website/service will be sent to your device from a VPN server.

In the simplest words, a VPN works as an intermediary between you and the destination website/Internet service. So, for your ISP, for instance, all the traffic from your computer/device will seemingly go to the VPN, not the website/Internet service you are trying to browse. In addition, because a VPN server can be placed in various places, VPNs allow users to bypass geographic content restrictions.
For instance, if a particular website/section of a website is not available in a certain country, the user can connect to a VPN server in a different country and get the job done. VPNs are a great way to protect your privacy and prevent data theft when you use a public WiFi network. When connected to a VPN, hackers/attackers cannot spy on your activities or the information you share.
Because many different VPN services are available, they also tend to offer additional features. For example, an instant Internet kill switch and two-factor authentication are commonly-included features. You can also pick one of the many encryption protocols based on the requirements. In addition, many VPNs allow you to choose between a high number of IP addresses so that you do not get caught.
However, it is not like VPNs are perfect. There are advantages and disadvantages to this piece of tech.
Pros of VPNs
- Compared to other forms of security systems, VPNs are easy to use. Once you have configured a VPN app, you can connect to the desired server with a single click. From then on, all your Internet traffic will be tunneled through the secure server.
- VPNs also provide you with better anonymity on the Internet, primarily because your IP address is being hidden. It also means you can access the content you cannot access using your actual profile. It is one of the reasons you can access geo-restricted content with the help of a VPN.
- The biggest advantage of a VPN is that your traffic is encrypted using military-grade security. It means the data you share with websites will not be leaked. It is one reason why enterprise users heavily rely on VPNs.
- Some users find VPNs useful for niche needs like gaming. For instance, if you have a good connection, it makes sense to connect to a VPN closer to the gaming servers instead of playing without a VPN. As a result, it can make the gaming experience smoother.
Cons of VPNs
- VPNs generally impact browsing and download speeds. Unless you have a fast Internet connection, you will notice a drop in the overall speed. It may not be convenient if your work requires the highest connection/download speeds.
- Dropped connections and IP bans are also not uncommon while using VPN services. In addition, since thousands of users use VPN servers, Internet services may block the IPs, causing problems in the long run.
Proxy Servers – A Quick Introduction
Proxy servers are also used to enhance anonymity and security while using the Internet. However, even though proxy servers and VPNs share some similarities, there are specific differences. Both proxy servers and VPNs work as intermediaries between a user and an Internet service, but you cannot expect features like encryption and customizability from a proxy server.
Because proxy servers work as intermediaries, the working process is similar to that of VPNs. These servers will receive web requests from your computer and forward them to the web server. Similarly, the response from the web server will be relayed back to your computer. Because the request comes from the proxy server, it would seem that the user is not involved in the process.
In this way, proxy servers can offer some degree of anonymity on the Internet. Similarly, because the server is placed in a different location, proxy servers can help users unlock geo-blocked content. For instance, if you live in the USA but are connected to a proxy server in another country, you can access content locked to users from the USA.
It is also essential to choose between regular and high-quality proxies. Because proxy servers are easily marked and restricted, you may face issues with standard proxy servers. As a result, there could be some accessibility issues. At the same time, people use these services to access several benefits, including content control and caching performance.
Types of Proxy Servers
Depending on their primary use, proxy servers belong to different categories. The major categories of proxy servers are:
- Reverse Proxy Servers
- Web Proxy Servers
- Anonymous Proxy Servers
- High Anonymity Proxy Servers
- Transparent Proxy Servers
- Suffix Proxy Servers
- CGI Proxy Servers
- Distorting Proxy Servers
- TOR Onion Proxy Servers
- I2P Anonymous Proxy Servers
- DNS Proxy Servers
You can also categorize proxy servers based on the protocols they use. Some of the available options are:
- Socks Proxy Server
- HTTP Proxy Server
- FTP Proxy Server
- SSL Proxy Server
You need to choose the right type of proxy and protocol based on your needs. For instance, you might need SSL or FTP proxy servers if you want to benefit from relaying and associated features.
Pros of Proxy Servers
- As VPNs, proxy servers can also provide anonymity by masking your IP address. Therefore, if you are worried about IP address-based tracking, you can stay safer by connecting to a proxy server. Of course, the level of your anonymity will vary based on the type of proxy in use.
- Even though encryption is not involved, proxy servers offer an additional layer of protection. Because all your web requests are forwarded through proxy servers, you are less likely to encounter digital threats, including malware.
- Proxy servers can help you bypass geography-based restrictions without a huge impact on the connection speed. In addition, because there is no encryption, you have a better chance of keeping your Internet speed high. It is also an excellent option for accessing remote content.
- Proxy servers are also great in that you can get performance boosts. Some proxy servers are equipped with caching systems more effectively than regular ISP servers. As a result, you may get better speed while accessing web pages.
Cons of Proxy Servers
- The anonymity offered by proxy servers is limited. They are vulnerable to being tracked, and the level of encryption used by proxy servers is not powerful enough in most cases. So, proxy servers are not the best option when you need the best protection.
- Configuring proxy servers and managing many of them can be cumbersome. It must also be clear that proxy servers are not as smooth as VPNs. It means you have to spend a considerable amount of time setting things up.
Anti-Detection – A Quick Introduction
Anti-detection technology, most often implemented through multi-accounting (anti-detect) browsers, deals with a significant aspect hampering online privacy: browser fingerprints. Whenever you interact with the web, information about your browser/device is shared with web servers, and this information can be used to detect and track users.
Anti-detect browsers can bypass this issue by spoofing (changing) browser fingerprints. Therefore, even if you use Google Chrome on a Mac device, you can make your browser fingerprint look like you are using another device. In addition, using high-quality multi-accounting anti-detect browsers like Octo Browser, you can create multiple simultaneous profiles mimicking different environments.
In addition to providing better anonymity on the Internet, anti-detect browsers can be used for various other needs. For instance, imagine that you want to use multiple social media accounts on a single device. Then, you can use an anti-detection browser and its different profiles to ensure your device is not restricted/banned by security systems.
Similarly, people who work in affiliate marketing and device-based testing also love the features offered by anti-detection browsers. In simple words, an anti-detection multi-accounting browser is an effective way to bypass the many solutions web servers have employed to prevent anonymization by users. Because of this, using an anti-detection browser becomes an essential part of the three-way method of safer web browsing.
Now that you know the basics of VPNs, proxy servers, and anti-detect browsers, we will discuss using them together.
How to Use VPN, Proxies, and Anti-Detection Together?
We must follow a three-step process to use VPNs, proxies, and anti-detection browsers together.
In our example, we have chosen one of the best anti-detect browsers – Octo Browser.
Step One
In this step, you have to set up and connect to a VPN server. You can choose one of the best VPNs based on your requirements. Once you have registered an account, you can download the VPN client and connect to the desired server.
Once this is done, you can proceed with the second step.
Step Two
To set up proxy servers efficiently, we can use Octo Browser, a popular anti-detection browser. So, first, you have to download and install Octo Browser with a valid subscription plan.
- Open Octo Browser and let it download the required components.
- Now, go to the Proxies submenu, where you can see a list of available proxies.
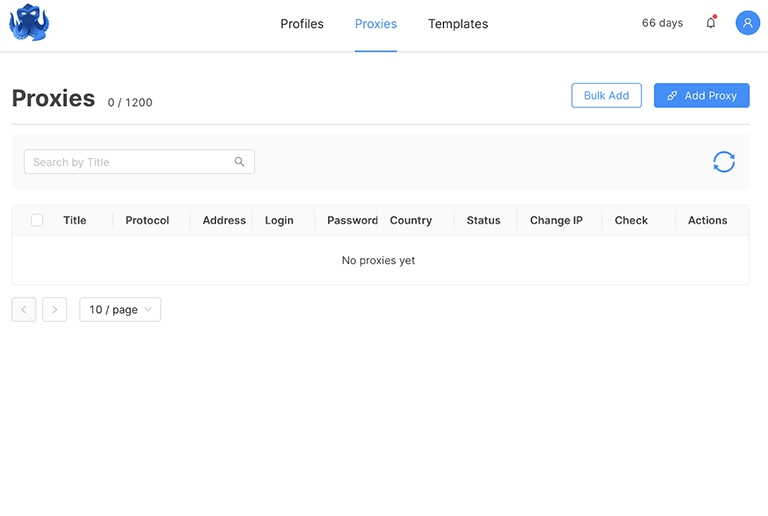
- Click the Add Proxy button to continue. Here you can specify the proxy name (optional), enter data about your proxy (type, host, port, login, password), add a URL to change the IP, and check your proxy.
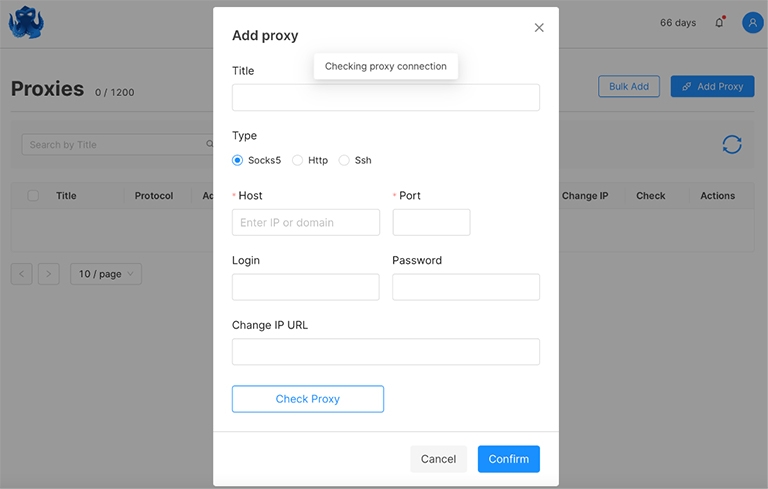
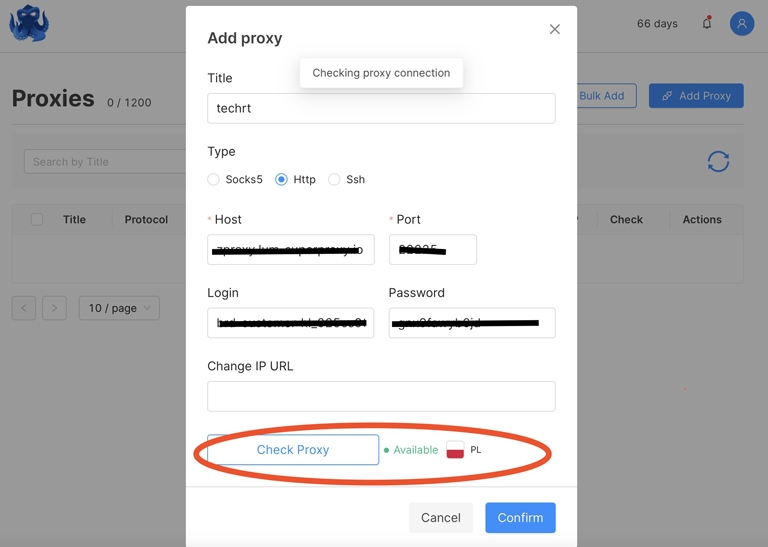
- Click the Check Proxy button, and Octo Browser will check the proxy server for potential issues and after that click “Confirm“.
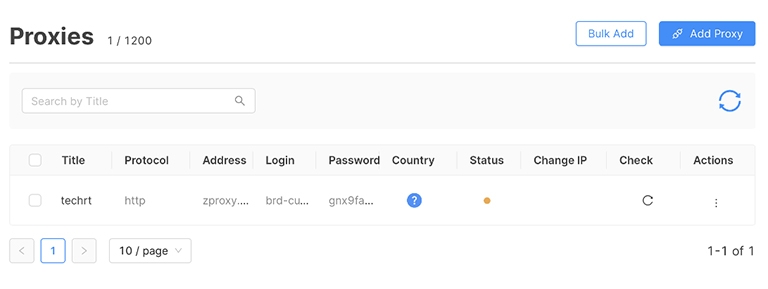
Once this step is done, you can see the new proxy on the list. You can shift between the available proxies when needed. Proxy statuses help you quickly understand what state the proxy is in.
There are 3 types of status:
Green – the proxy has been successfully verified.
Yellow – the proxy has not been verified, or the last verification was more than 5 minutes ago.
Red – the proxy cannot be verified and you should contact your proxy provider.
Step Three
In this step, we have to create an anti-detect browser profile and set things up. In Octo Browser, you can have as many profiles as you’d like. To create one,
- Go to the Profiles page and click the Create Profile button or Quick Profile button.
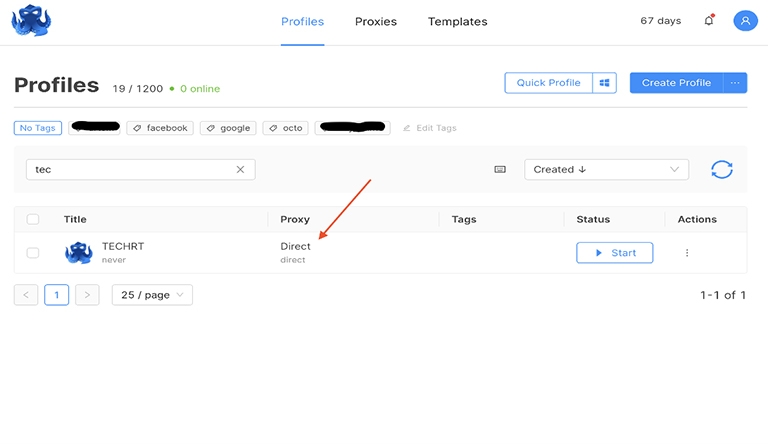
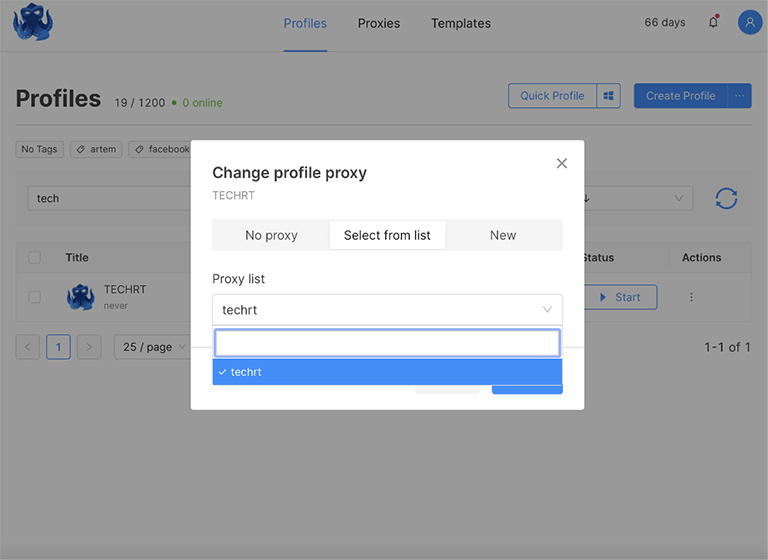
- After you have created a profile, you need to click the Direct button. You can select a previously saved proxy or enter data for a new one.
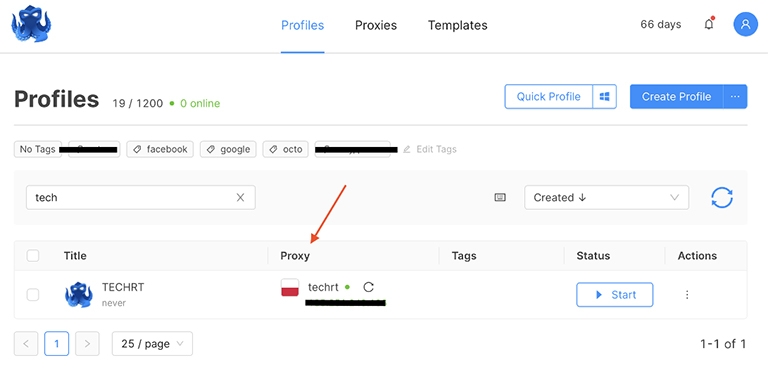
- After that, information about the selected proxy appears in the “Proxy” section of your profile.
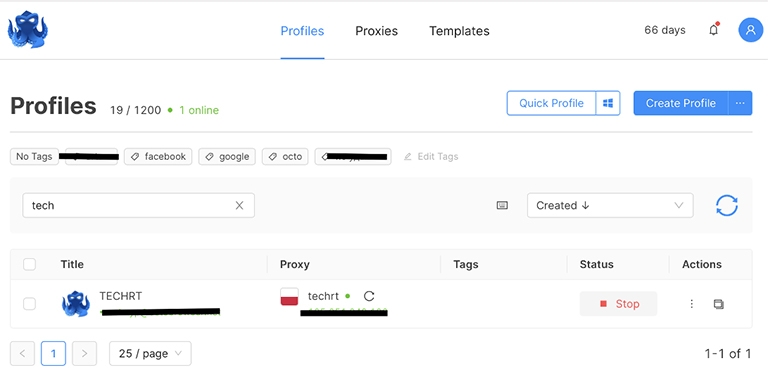
- Now you can click “Start” and be completely sure of your anonymity online.
You can continue using the browser as you normally would — but without worrying about detection, blocking, and other issues.
Important! Sometimes when using a multi-accounting browser together with VPN and proxies, you might notice that the connection becomes slower. This is usually caused by data having to travel further. However, sometimes a connection through a remote IP address can even increase the connection speed: this happens when a provider downgrades the connection for specific sites on purpose, but a VPN- or proxy-assisted connection hides your visits from the provider.
Conclusion
As you have seen, using an anti-detection multi-accounting browser together with VPN and proxy servers can help you achieve maximum protection on the Internet. In addition to boosting your anonymity, this setup is also effective for professional needs like affiliate marketing, mass social media management, etc.
We have used Octo Browser, one of the best anti-detection browsers, to manage anti-detect profiles and proxy servers. We have picked Octo Browser for many reasons: first, Octo Browser is easy to use and set up. Secondly, you do not have to worry about security concerns thanks to timely and regular kernel updates and speed.
But more importantly, Octo Browser works smoothly on almost all devices, namely on operating systems such as Windows, macOS, and Linux. Because it uses the Chromium browser engine, you can efficiently work with the UI: it’s very similar to using Google Chrome.
So, what do you think about our method of staying safe on the Internet? Do let us know in the comments!



Leave a comment
Have something to say about this article? Add your comment and start the discussion.